After completing the CEH, I immediately set my sights on the OSCP.
That’s the Offensive Security Certified Professional. It is notorious for its 24-hour long exam and (suspected) low pass rate, as well as its challenging course labs.
All the cool nerds want this cert. That includes me, of course! I MUST HAVE IT.
The course is intense and not very flexible
They require you to book your lab time in 30, 60, or 90 day blocks without being able to pause that time under normal circumstances. This differs from the self-paced learning options offered by other online courses. I have a toddler son, a wife, and a full-time software development job, so my free time for hanging out in my home office pwning n00bs (off-the-clock) is a bit limited these days.
I want to be able to make the most of the course time when I do officially start it, and hopefully get it all done in one shot (the course work at least, if not the exam.)
I’m posting this here to motivate myself to follow through.
Preparing for the PWK Course
The course that precedes the OSCP cert is Penetration Testing with Kali (PWK.) To prepare for that course I plan on working through the following steps (which are subject to change as I learn more.)
Vulnhub VMs
From what I have gathered, the best way to prepare for the course is to take on similar VMs in a home lab. Vulnhub has tons of these available for free.
I had completed 4 of them in the last month (not listed here), but needed to check for quick hints at a couple steps. As the OSCP mantra is “TRY HARDER,” I will finish more of these with no help whatsoever. They will be featured in a series of walkthroughs.
These are the ones I’m starting with for now. They were originally sourced from here, and will be tweaked over time.
| Name | My Solution | Rooted |
|---|---|---|
| Kioptrix 2 | Walkthrough | 2018-03-20 |
| Kioptrix 3 | – | 2018-03-22 |
| Kioptrix 4 | – | 2018-07-13 |
| Kioptrix 2014 | WIP | 2018-07-15 |
| Pinky’s Palace: v1 | WIP | 2018-09-29 |
| FristiLeaks: 1.3 | WIP | 2018-10-14 |
| Staper 1 | Walkthrough | 2018-09-28 |
| PwnLab: init | – | 2018-09-27 |
| Brainpan: 1 | – | – |
| Mr-Robot: 1 | WIP | 2018-09-24 |
| HackLAB: Vulnix | – | 2018-10-13 |
Hack The Box
This is awesome! I should have started with it way sooner.
You have to solve a simple challenge to get in, then you get access to their network by VPN and have an assortment of boxes to practice on, all ready to go with no setup required on your end. I’ve popped a few of them so far.
One big advantage of HTB over Vulnhub is that there’s plenty of Windows machines, which I haven’t been able to practice much with until now. A disadvantage is that you need to be mindful of other people trying to work on the same machines as you. I’ve found it’s not a big deal to work around. Link: hackthebox.eu
Cybrary.it Courses
Python for Security Professionals
Advanced Penetration Testing
Metasploit Unleashed
The free course by Offensive Security
Update!
This blog post inspired me to just sign up and get started.
I know enough to start and will learn more as I go, in the lab. My labs start on November 3rd, 2018.
I will be watching IppSec Youtube Videos in the meantime to pick up some new techniques to try.
Update 2! 2018-11-22
This is so much fun! I have popped 17 lab machines so far. None of the “boss” machines yet, but those will fall in time. I wish I could spend more time on this but it has to be limited to evenings after work.
In Hindsight…
For my preparation, I should have read Georgia Weidman’s book and quickly went through her Cybrary video course linked above. I skipped over her stuff prior to the course because the content seemed dated, but as it turns out, it would have been just fine for OSCP preparation.
PWK takes a “walk before you run” approach to hacking, and a lot of the older operating systems are quite helpful in that regard. They do make an appearance in PWK.
Windows…
There’s way more Windows machines in the lab than I was expecting. In fact, it’s been the majority of what I’ve worked on so far.
Definitely brush up on Windows privilege escalation if you can, though you can always learn it as you go in the labs. This is a course, with actual training materials, after all. And there are hints on the forum and in IRC if you get stuck, so you’re not totally on your own.
Again, hackthebox has some Windows machines to try out. I’ve found htb to be harder than PWK machines so far, so don’t worry too much if you’re finding htb to be challenging (it is!)
Don’t be afraid of hints
I went in with the attitude that I was going to exhaust all possible ideas before ever looking for hints, TRY HARDER, etc, but that was silly.
The hints are subtle, but they are enough to put you on the right track so you’re not wasting your time on something that will never possibly work. After reading a hint, you still need to figure out what exactly they are referring to, and how to make that work with the machine you’re working on. There’s still plenty of opportunity for learning.
Just make sure you are learning and understanding from every single box, or else you’re cheating yourself.
From what I hear, the more machines you pwn, the more tricks you’ll learn, and the better your chances of passing the exam without multiple attempts. So pwn more boxes, that’s all there is to it. If you need hints here and there to make that happen, so be it. If your time is limited, give each box a fair shot first, then check for hints if you’re still stuck after a reasonable amount of time. My current threshold before checking for hints is about 2 hours of zero progress.
Sometimes I sleep on it and figure out the solution right away the next evening. But the point is, be efficient with your lab time and pwn as many boxes as you can.
Again, regarding endless “preparation” for OSCP
There’s nothing to fear if you meet the basic requirements listed by OffSec.
Maybe power through Georgia’s book/course, and take down a few Vulnhub VMs or HTB machines. But then go sign up!
No more procrastinating, you got this!
Update 3!
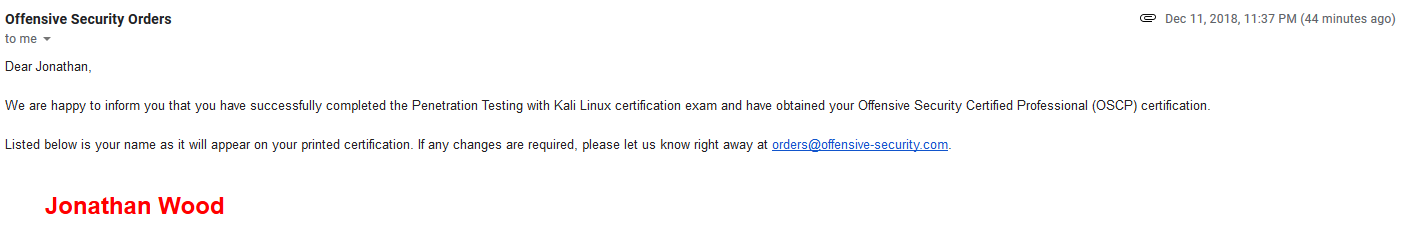
I decided to schedule my exam early, after only 35 days of lab time and 31 rooted machines. The labs had been going well so I thought it would be challenging, but not impossible.
Well, it worked out. I passed! Rooted 4 boxes and got a low priv shell on the 5th. I’ll do a proper write-up later in a new post.

I realize this is an 6 month old post, but came across it googling Info for the OSCP. I am also starting November 3rd, so looks like we’ll be going through this together. Feel free to drop me an email and we can compare notes, help each other out when we get stuck.
Sounds good, will do. I’m stoked, can’t wait!